October 17, 2015: We are receiving reports about massively infected Magento sites with GuruIncsite Javascript malware function LCWEHH(XHFER1)…..On October 20, 2015 Magento sent announce to all Magento installations via news feed in backend:
New Malware Issue. Make Sure You Have Implemented All Security Patches We have received reports that some Magento sites are being targeted by Guruincsite malware (Neutrino exploit kit). We have NOT identified a new attack vector at this time. Nearly all the impacted sites checked so far were vulnerable to a previously identified and patched issue; sites not vulnerable to that issue show other unpatched issues. Visit the Magento Security Center at http://magento.com/security/news/important-security-update for more information on how to address this issue and make sure that you have implemented all recent security patches.The complete malware code is added to footer through miscellaneous HTML in Magento admin, it starts like
(function(){function LCWEHH(XHFER1){XHFER1=XHFER1["\u0073\u0070\u006c\u0069\u0074"]("");var.
Another modification of the code is not obfuscated. Both modifications load guruincsite.com site.
Soon after the hack you may receive notification from Google with Malware infection detected subject, which means that Google has blocked access to your site with “Reported attack page” blocker:
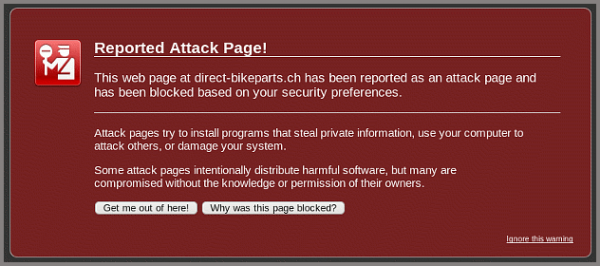
Mitigation
To mitigate the GuruIncSite malware- navigate in Backend to System > Configuration > Design > Footer > Miscellaneous HTML and delete all code there:
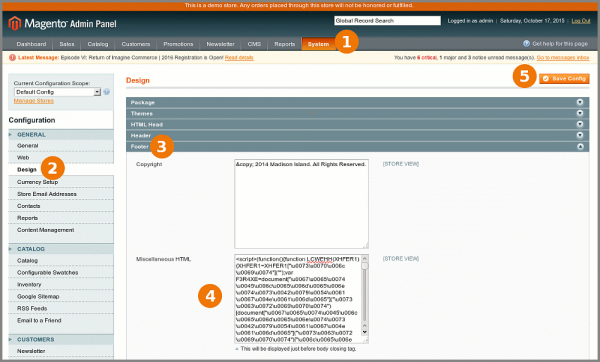
Removing GuruIncSite Malware code from footer in Magento - Navigate to CMS > Pages > Home > Content in Backend, click Hide Editor to switch to code view and delete malicious code between
<script>and</script>tag (selected on the screenshot):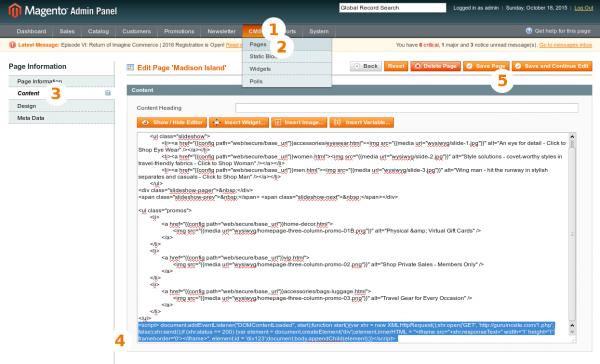
Deleting Malicious code (selected) from CMS Home page - IMPORTANT: Navigate to System > Magento Connect > Magento Connect Manager and check for updates. Update all third-party extensions, uninstall any non-used third-party extensions
- delete any unknown users at System > Permissions > Users
- Flush Magento cache to apply changes
- Scan your store with our security tester and ensure store is safe, GuruIncSite Malware not found. If not, repeat the steps above (for other CMS pages / static blocks / extensions)
- open Google Webmaster Tools and navigate to Security tab and confirm that the malware is removed to open access to your site for visitors:
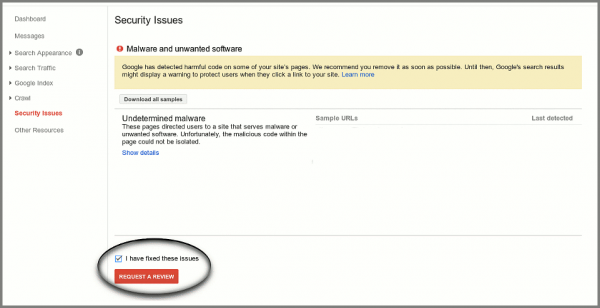
Confirm Malware removal and request Google’s review
- To prevent it from re-occurance Scan your store for unpatched vulnerabilities and install all patches or upgrade to the latest Magento version.
Posted in: Magento Maintenance